Security Roles
This information is for system administrators who are responsible for maintaining users in ProLink+.
Security roles dictate what users can and cannot see, as well as what functions they can and cannot perform. Each security role is associated with a functional area and specific authority for a screen, field, or button. This section of the system tracks all the different security roles and the access of the security role, as well as which users are associated to the security role.
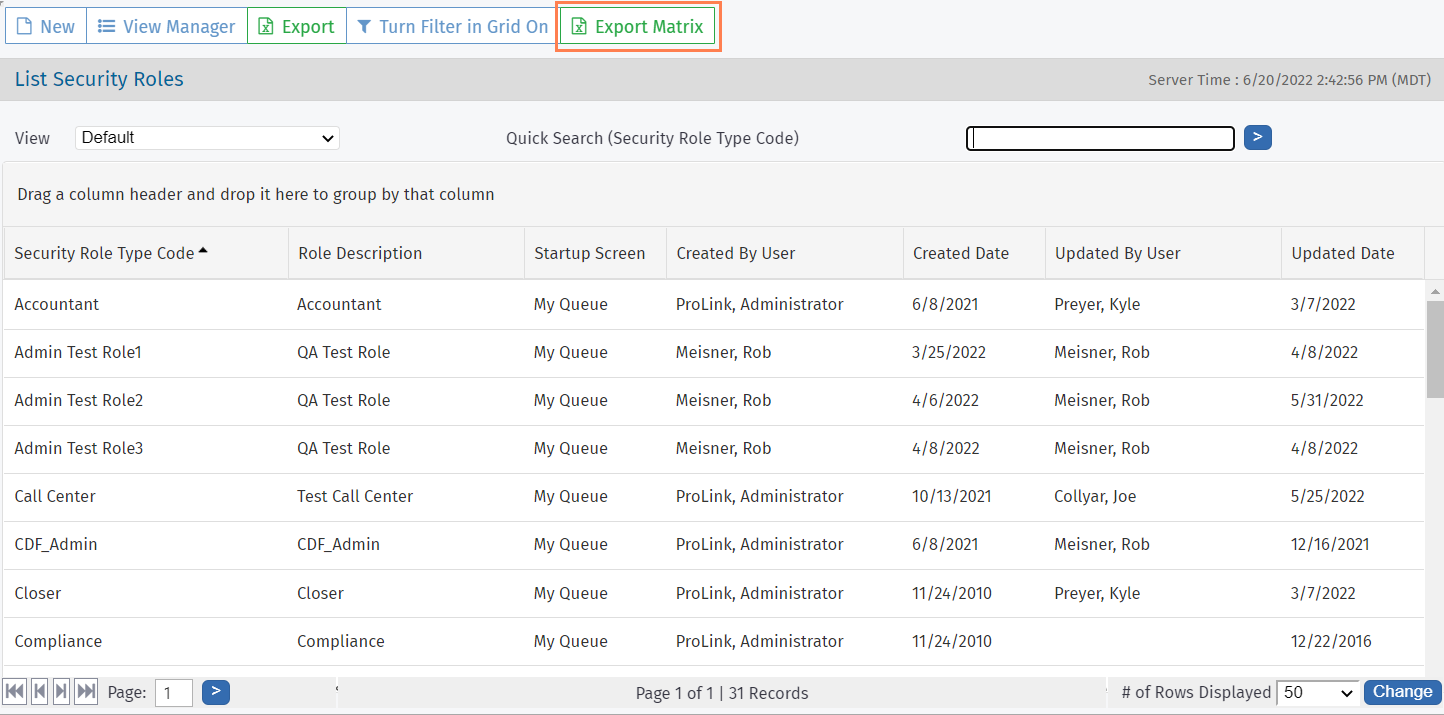
The screen is a data view screen, which means you can filter, sort, search, and create custom views, like with other data views.
Tip
Using Quick Search, search for a role by security role type or role description.
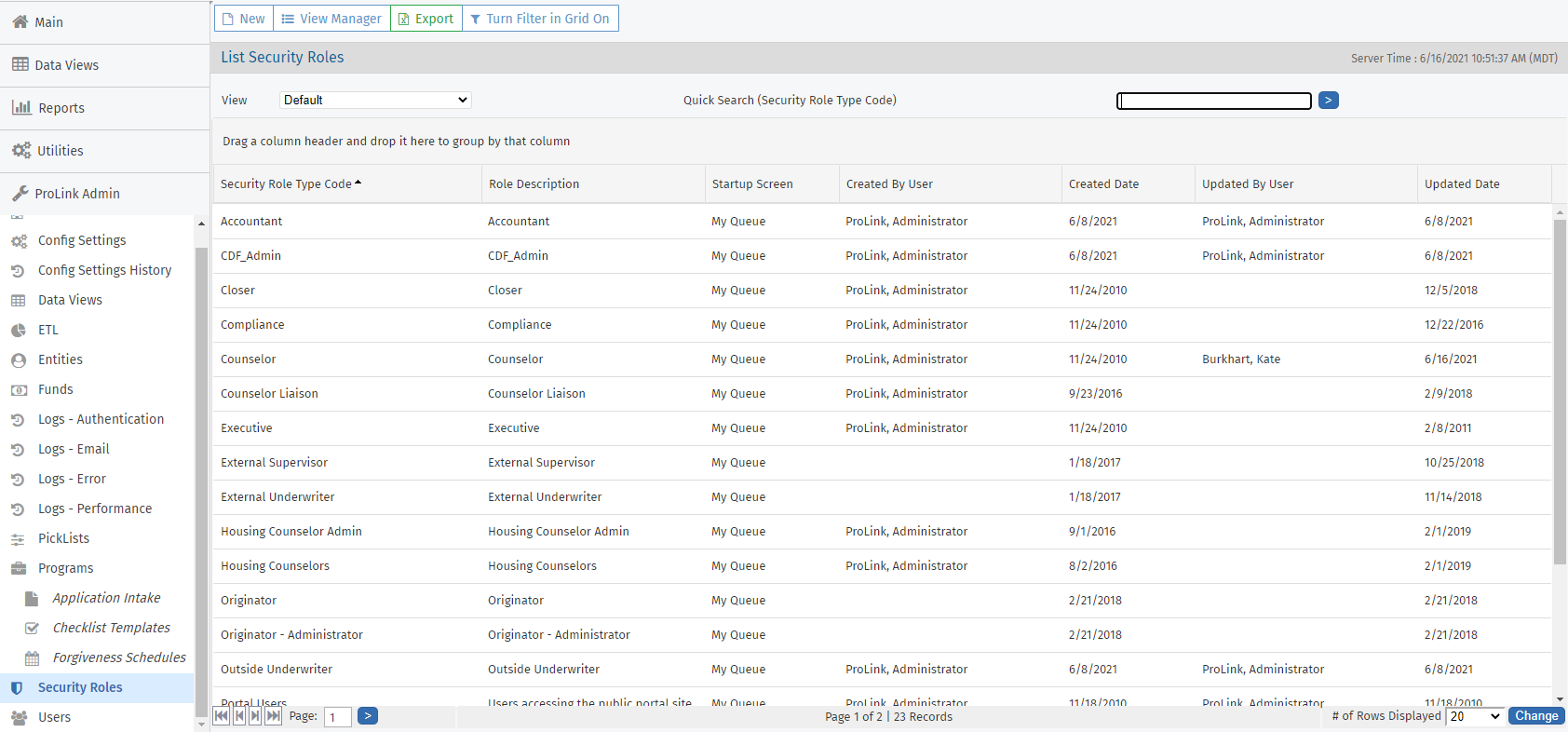
Click a row to open the Security Role record and view its details. The Edit Security Role screen opens.
Tip
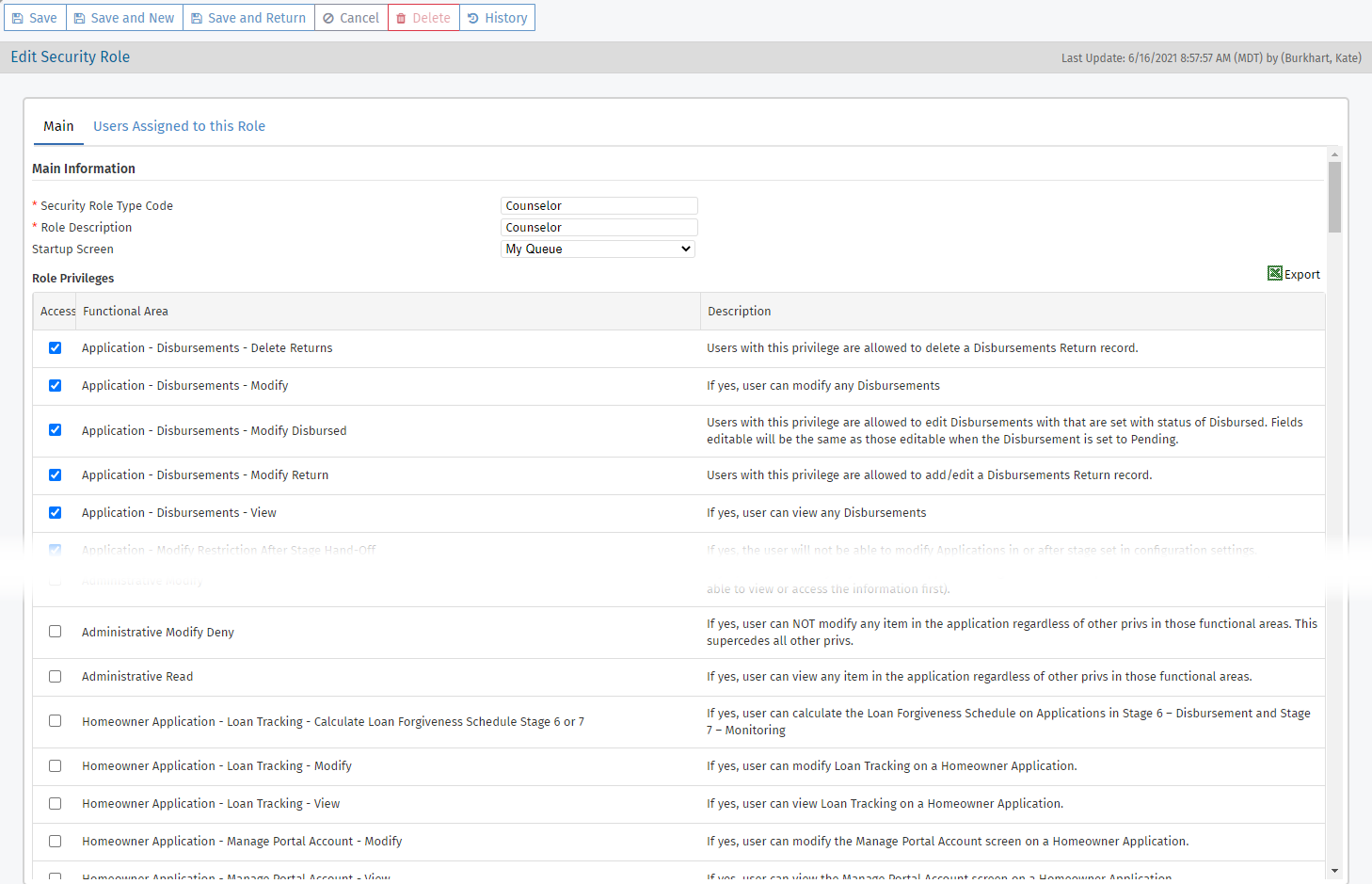
To see which users have been assigned to a specific security role, navigate to the Users Assigned to this Role tab. Clicking a row in the grid navigates you to the User record.

At implementation, your environment is set up with a default set of roles. You can modify or delete these roles, or add additional ones. A good way to review the allowed privileges for a role is to open the specific record and then export the role privileges grid information. Notice that the Access checkbox is selected for privileges included for the role, and these selected records are sorted alphabetically at the top of the list. Then the privileges not allowed follow, again in alphabetical order.
Setup and maintenance of security roles is an ongoing task for system administrators. Review the security roles with your agency's users in mind. You might need a simple set of roles, or you might need variations on a base set of roles. For example, perhaps all the Underwriters can have the same level of privileges. Or perhaps you have separate roles for internal and external Underwriters.
Remember to review the security privileges introduced with each release. Do you need to update any security roles to provide access to the new privileges?
Navigate to the Admin menu, and then select Security Roles (under Users) in the left navigation panel.
Review the existing security roles to verify an existing role doesn't satisfy the requirements of the new role already.
Click New in the top toolbar.
Enter the name of the role in the Security Role Type field.
Enter a description to help you remember the purpose of the role.
In the Startup Screen list, select which screen users assigned to the security role will see when they log in.
Select the Access checkbox for all the privileges that the role should have.
Notice in the description whether there are any dependencies for the privilege. For example, if you give permissions to delete checklist templates, then you also need to provide permissions to view checklist templates.
Click Save.
You can now assign the security role to a user(s). See Users for more information.
Caution
Keep in mind that the privileges for the security role provide access to the corresponding functional areas for every user assigned the role.
Important
The Admin Modify and ProLink Admin - User - Modify privileges are required to be able to copy a security role.
You can create a copy of an existing security role to help save time when creating a role that is similar to an existing role. Click Copy Role in the top toolbar to create a new role based on the existing role, called {copied role name}: COPY.
Be sure to save the copied role. It is committed to the database upon saving.
You can delete a security role if no users are assigned to the role.
Tip
To see which users have been assigned to a specific security role, navigate to the Users Assigned to this Role tab. Clicking a row in the grid navigates you to the User record.

Navigate to the Admin menu, and then select Security Roles (under Users) in the left navigation panel.
Click the row to open the Security Role record and view its details.
Click Delete in the top toolbar, and confirm the deletion.
The Export Matrix button in the top toolbar of the List Security Roles screen allows you to export a Microsoft Excel spreadsheet of all roles and their associated privileges, so that you can compare access across security roles.